⎈ Kubernetes CIS benchmarks analysis
🙌 Overview
This scenario is very useful in performing Kubernetes security audits and assessments. Here we will learn to run the popular CIS benchmark audit for the Kubernetes cluster and use the results for the further exploitation or fixing of the misconfigurations and vulnerabilities. This is very important and mandates if you are coming from an audit and compliance background in the modern world of containers, Kubernetes, and cloud native ecosystems.
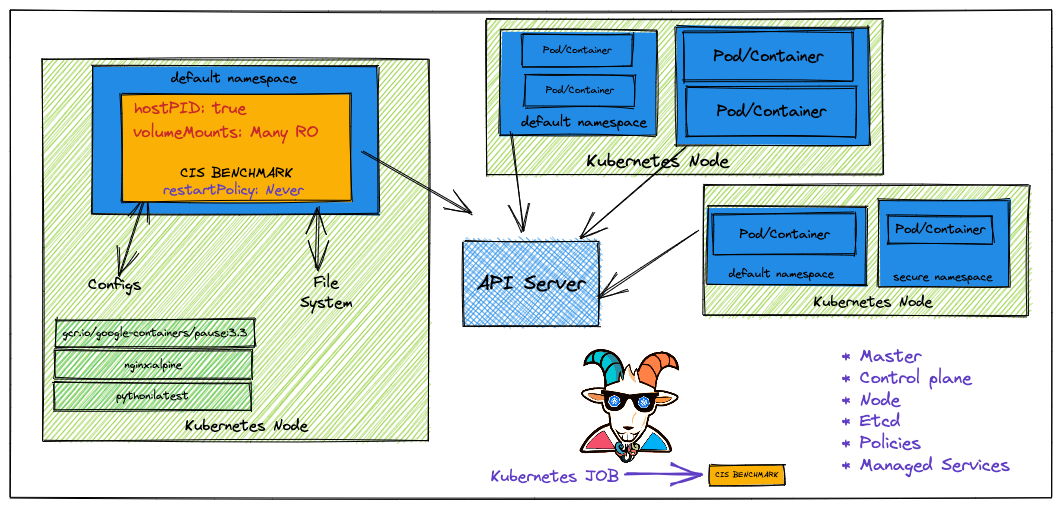
By the end of the scenario, we will understand and learn the following
- You will learn to perform CIS benchmark audit for Kubernetes clusters
- Working with jobs, Pods in Kubernetes, and other resources in the cluster
- Gain visibility of the entire Kubernetes cluster security posture and understand the risks
⚡️ The story
This scenario is mainly to perform the Kubernetes CIS benchmarks analysis on top of Kubernetes nodes and cluster resources to identify the possible security vulnerabilities.
- To get started with this scenario you can either access the node and perform by following kube-bench security or run the following command to deploy kube-bench as Kubernetes job
- To get started with the scenario, you can deploy the Kubernetes CIS benchmarks job using the following commands
kubectl apply -f scenarios/kube-bench-security/node-job.yaml
kubectl apply -f scenarios/kube-bench-security/master-job.yaml
🎯 Goal
The goal of this scenario is to perform the Kubernetes CIS benchmark audit and obtain the results from the audit.
🪄 Hints & Spoilers
✨ Not sure how to run the audit?
🎉 Solution & Walkthrough
🎲 Method 1
- We can deploy the Kubernetes CIS benchmarks by running the following command
kubectl apply -f scenarios/kube-bench-security/node-job.yaml
- Now we can obtain the list of jobs and associated pods information by running the following command
kubectl get jobs
kubectl get pods
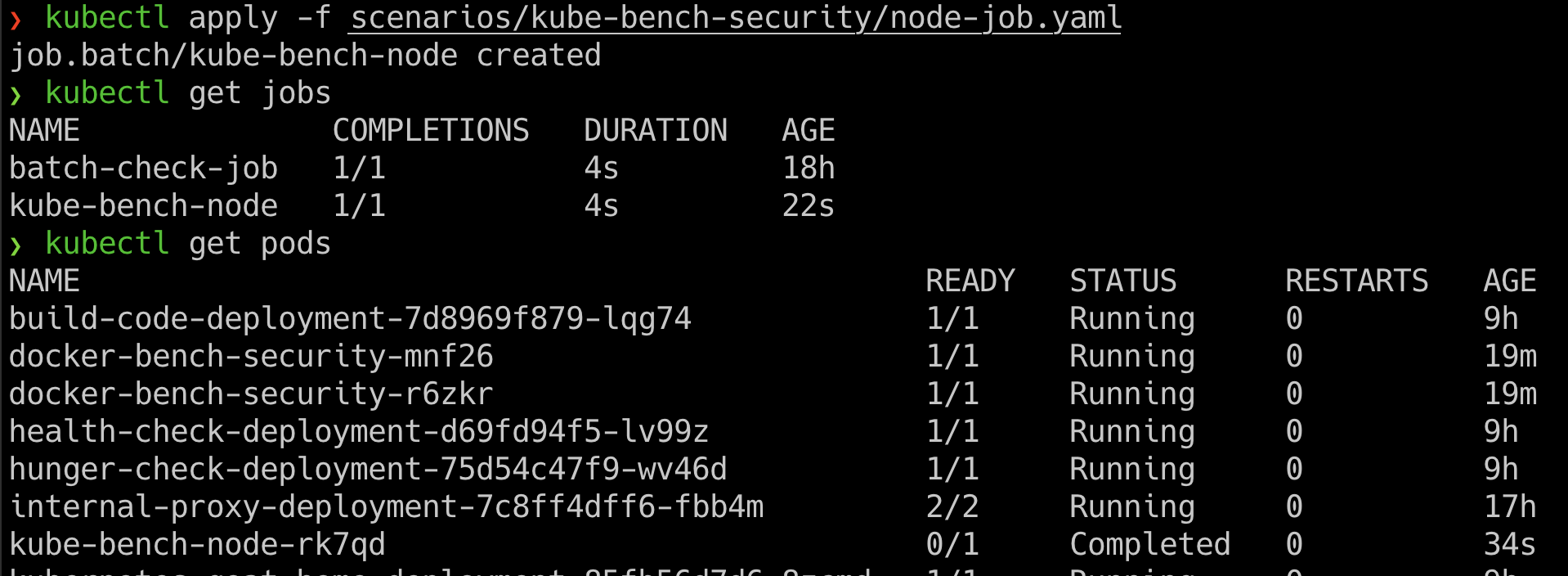
- Once we have identified the pod, then we can get the audit results by running the following command. Make sure to replace the pod name in the following command
kubectl logs -f kube-bench-node-xxxxx
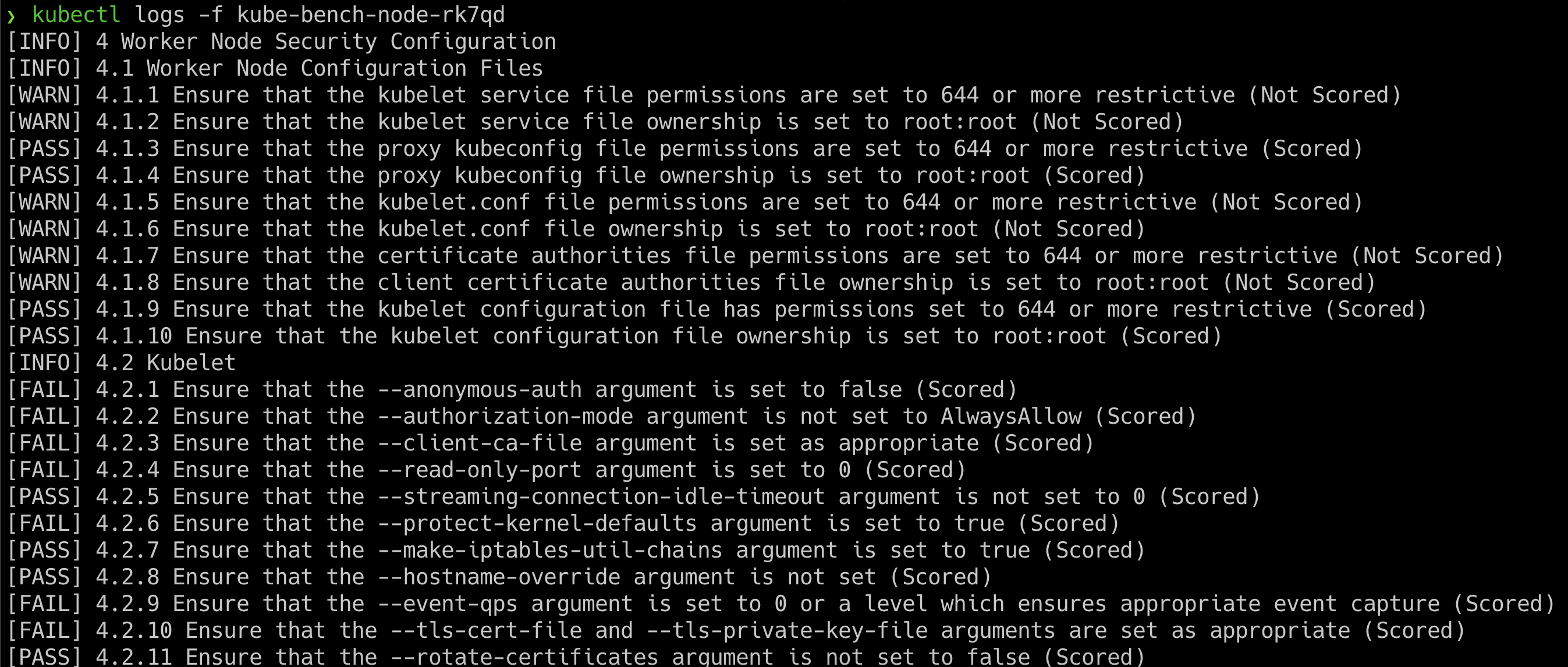
-
Now based on the vulnerabilities you see from the Kubernetes CIS benchmarks, you can proceed with further exploitation
-
Hooray 🥳 , now we can see that it returns the all security issues/misconfigurations from the cluster