⎈ Gaining environment information
🙌 Overview
This is no different from the traditional workloads. Most of the compute instances while running the applications store sensitive information like secrets, api_keys, etc. in the environment variables. Similarly, in Kubernetes, most of the people store sensitive information like Kubernetes Secrets and the Config values in the environment variables and if an attacker can find application vulnerabilities like RCE(remote code execution) or command injection then it's game over for that secret.
By the end of the scenario, we will understand and learn the following
- How to explore the environment variables and analyze
- Gaining access to sensitive information in the container
⚡️ The story
Each environment in Kubernetes will have a lot of information to share. Some of the key things include secrets, API keys, configs, services, and a lot more. So let's go ahead and find the vault key!
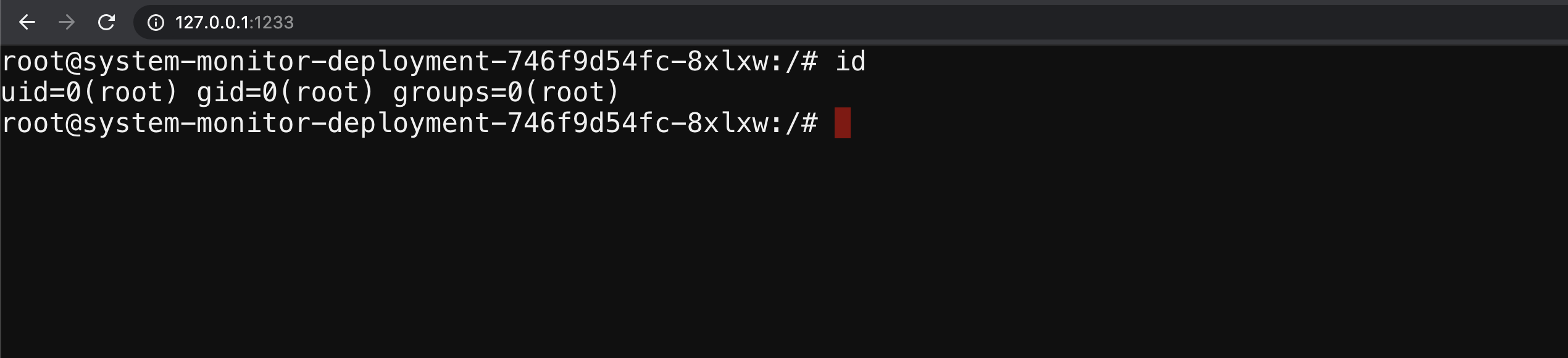
To get started with the scenario, navigate to http://127.0.0.1:1233
🎯 Goal
Get the k8s_goat_flag flag value then you have completed this scenario. This can be found in multiple ways!
🪄 Hints & Spoilers
✨ Not sure where the environment variables get stored?
🎉 Solution & Walkthrough
🎲 Method 1
-
We can explore the container by running different commands and understand the system much better. This is more like an exploration scenario to explore the container and understand it better
-
We can get the container runtime information by running the below command
cat /proc/self/cgroup
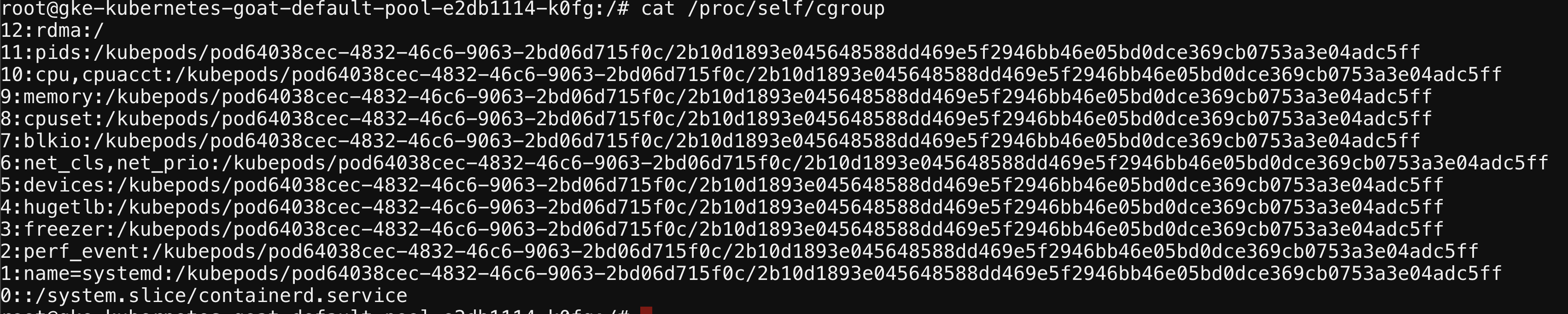
- We can get the information of the container host's information
cat /etc/hosts
- We can get the mount information
mount
- We can also look and explore the file system
ls -la /home/
- We can access the environment variables, including Kubernetes secrets mounted and service names, ports, etc.
printenv
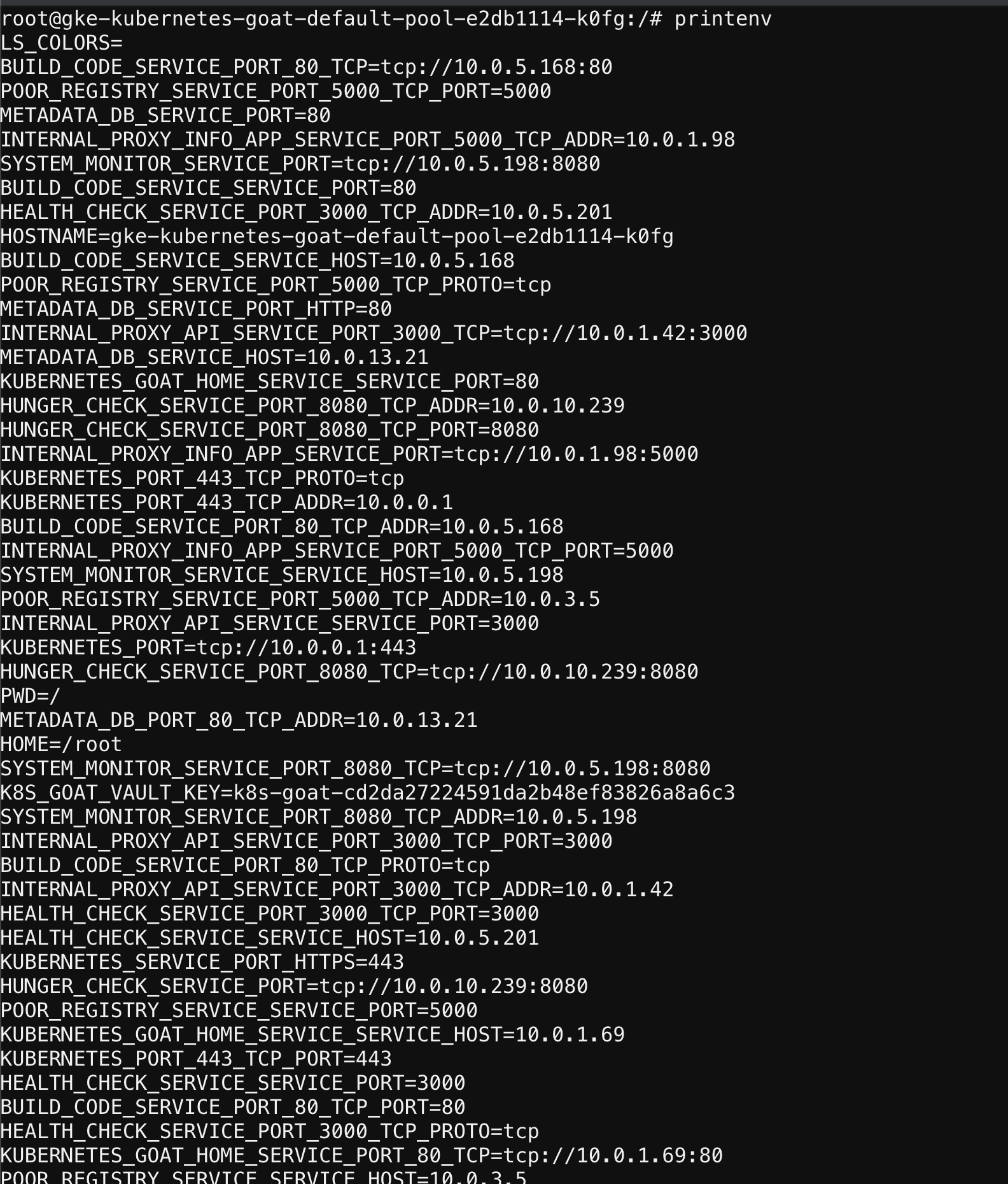
- Hooray 🥳 , now we can see that it contains the Kubernetes Goat flag which is mounted as a Kubernetes secret inside the pod/container